通过编辑coredns configmap
apiVersion: v1
data:
Corefile: |
.:53 {
errors
health {
lameduck 15s
}
template IN A *.google.com {
answer "{{ .Name }} 60 IN A 183.60.xx.xx"
}
template IN A google.com {
answer "{{ .Name }} 60 IN A 183.60.xx.xx"
}
template IN A *.googleapis.com {
answer "{{ .Name }} 60 IN A 183.60.xx.xx"
}
template IN A googleapis.com {
answer "{{ .Name }} 60 IN A 183.60.xx.xx"
}
ready
kubernetes cluster.local in-addr.arpa ip6.arpa {
pods verified
ttl 30
fallthrough in-addr.arpa ip6.arpa
}
prometheus :9153
forward . /etc/resolv.conf {
prefer_udp
}
cache 30
log
loop
reload
loadbalance
}
kind: ConfigMap
metadata:
name: coredns
namespace: kube-system
重启coredns
kubectl -n kube-system rollout restart deployment coredns
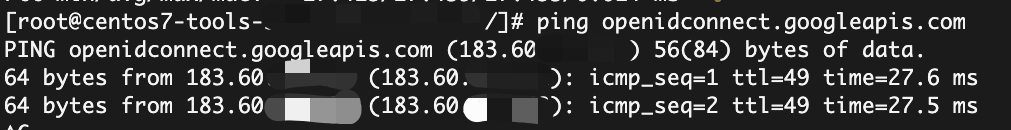
随便找个容器ping下,成功解析到指定的ip上

评论区